Fingerprint or sometimes footprint is a digital representation of a user’s device consisting of information about your operating system, settings, active browsers, installed plug-ins, etc. Such a fingerprint is generated as a unique code or image.
If you use proxies to increase your browsing anonymity, you need to match your proxy-related parameters with the current fingerprint attributes.
In this article, we will cover some of the most useful practices shedding some light on the type of ‘fingerprints’ that your browser leaves on the web and ways to successfully increase your anonymity.
Types of Fingerprints
The way fingerprinting works is through collecting information on your system that increases its ‘entropy’ (i.e. uniqueness), so it becomes easily identifiable by the website. The fingerprints your browser and computer leave on a website reveal a surprising amount of information about the user. It includes a whole number of parameters ranging from the browser user agent, operating system version and browsing history to screen resolution, WebGL renderer, device IDs, network IPs, WebRTC and even battery info.
Browser-Based Fingerprints
- Current IP
- Browser headers (User-Agent, HTTP, ACCEPT, Do Not Track)
- JavaScript screen parameters
- Information about cookies and ‘super’ cookies enabled or disabled in the browser
- Installed browser plug-ins, their versions, and updates
In addition to browser-based fingerprints, you should also be aware of the cross-browser fingerprinting. Modern fingerprint trackers will collect and analyze information from different browsers using the same hardware and easily identify the end-user.
Cross-Browser Fingerprints
Cross-Browser Fingerprinting allows tracking the following:
- Operating System
- Number of cores in the processor
- List of fonts and installed languages
- Analysis of responses to operations performed by the browser involving the operating system and hardware components (2D and 3D rendering of shapes and pictures, creating shadows, etc.).
Such data is browser-independent.
Fingerprinting: Description
In the section below we describe all features of your system that leave fingerprints tracing back to your software and hardware settings.
Browser User-Agent
User agents are obvious fingerprints of your system. The browser user-agent is intended to facilitate end-user interaction with web content and it is part of the request header that contains more information such as the accepted language and accepted text/html.
The user-agent format in HTTP consists of a list of product names and versions.
For example: Mozilla 5.0 and layout engine and version, for example, Gecko 1.0
Cookies
Cookies are an older form of web storage in the browser. They were originally intended to store data received from the server in one request and send it back to the server in subsequent requests. But from JavaScript, you can use cookies to store just about any kind of data, up to a size limit of 4 KB per cookie.
Сookies are only relevant within the same domain. All cookies, including evercookies, can be easily cleared or blocked through a set of easy actions. From the perspective of fingerprinting, standard HTTP cookies can be easily deleted from the system once you set your browser into the ‘incognito’ mode.
Web Storage
Web storage is a mechanism for JavaScript to store data within the browser. Like cookies, web storage is separate for each origin. Web storage is completely invisible to the server, and it offers much greater storage capacity than cookies.
There are two types of web storage: local storage and session storage. An item of local storage is visible across all tabs of all windows and persists even after the browser is closed. It behaves somewhat like a cookie with an expiration date very far in the future. An item of session storage, on the other hand, is only visible within the tab where it was created, and it disappears when the tab is closed.
Canvas API
When you visit a website a special fingerprinting script draws a sample text with font and size of choice and adds a background. This text may contain 2D objects and emojis. Then the script reads the rendered image data back to compare pixel precision.
The same shape or text will be rendered in different ways on different computers depending on the operating system, font libraries, graphic card, graphics card driver and the browser.
WebGL
WebGL works in a way similar to Canvas but renders interactive 3D objects in the browser without the use of plugins.
The website may gain info on your graphics card vendor and model. This indirectly leaks the operating system as Windows or Mac OS.
WebRTC
The WebRTC (or web real-time communication) nodes are used for collecting info on IP addresses for providing the best routes between two peers in the network. If leaked, this info can be easily used for fingerprinting.
If you use browserleaks.com to test your system, you will be able to see your network IP and below the webRTC detecting the ethernet address in your office, along with device IDs. Make sure to turn-off your webRTC to avoid IP leaks when using a proxy through a browser.
Fingerprinting: Remedies
Below we have listed all common ways to overcome the problem of digital fingerprinting to ensure anonymous browsing.
VPNs and Proxy Servers
VPN or proxy is the easiest method to bypass regional restrictions. It changes your IP to the one available on the service.
However, proxies on their own, do not protect against multiple trackers and don’t affect the cookies already in your system. It is true even if you are using some of the best datacenter proxies. And that’s why it’s important to complement your proxy usage with additional manipulations with your fingerprints. This applies to all types of proxies (rotating datacenter proxy or a residential IP).
Manual Settings
To make your fingerprint less unique, you might want to tweak the following settings manually.
- Change the time zone of your device;
- Setting a different language for the device operating system;
- Set a different language for your browser;
- Change the resolution of the device screen;
- Change the viewing scale (zoom in/out) on a web page;
- Install or remove browser plug-ins;
- Disable Flash, Javascript, and WebGL.
Some may find these methods radical and somewhat inconvenient for surfing but, nevertheless, it helps significantly improve your browsing anonymity.
Tips and Recommendations
If you are using Firefox or Chrome, the following recommendations will be right for you to ensure anonymous surfing.
Consider installing the following plug-ins to increase your browser’s anonymity:
User Agent Switcher – swaps the user agent of the browser.
Ghostery – blocks analytics trackers, ads and other beacons.
Besides the plugins, you should always disable WebRTC on your computer. It is important to prevent the IP leak of your local IP subnet. In most cases disabling WebRTC will not affect the website behavior and will not block you.
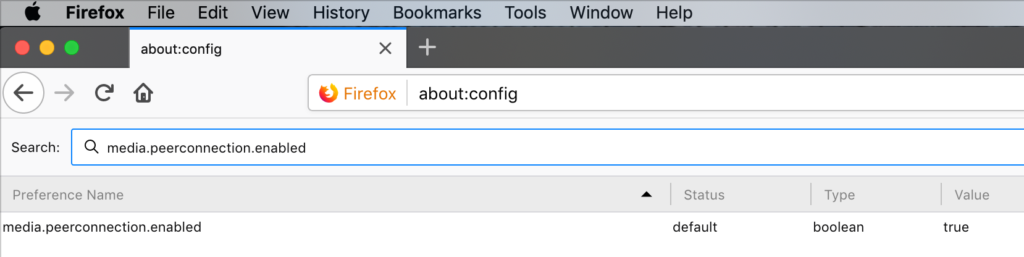
To do that in Firefox type about:config and search for media.peerconnection.enabled., and set it to false or search for some plugins to do the job.
In Chrome you can install the extension WebRTC Leak prevent extension. Or type: chrome://flags/#disable-webrtc
Furthermore, you should disable all JavaScript options, 3D software rasterizer, all GPU functions, all WebGL options, disable pixel canvas recording, etc.
In Firefox, you just need to type about:config and disable the above attributes. Otherwise, this can be done by adding noscript plugin to block scripts that run on the browser.
In Chrome this can be performed by typing chrome://flags and going over the list and disabling: Accelerated 2D canvas, Composited render layer borders, Tint GL-composited content, Enable draw occlusion, all options mentioning WebRTC.
Should you need more information on how to use proxy in Chrome, follow this link to find out.
Anonymous Browsers
There are also some specially assembled browsers for anonymous web surfing such as Pale Moon, an open-source browser based on Firefox, Selenium or Puppeteer.
When working with anti-detect browsers you can choose to block some of the fingerprint utilities as some target sites will allow access without any fingerprint data. To do this you disable Java, remove Flash, disable WebRTC, WebGL, and canvas.
You can also use Multiloginapp or SessionBox, platforms designed to swap different browser fingerprints. These programs are designed to work with a large number of browser profiles. Each profile is placed in its own “container” eliminating the risk of leaking browsing history, cookies, and fingerprints between the profiles.
However, some target sites might block you when you remove some fingerprints features and can return null data.
You should also note that when you use some browser automation tools to emulate a desktop or mobile users, it is important to replace the headless browser user-agent. For example, using Puppeteer that utilizes Chromium, the user-agent includes the string “HeadlessChrome”, which is easy to detect.
Replacing the user-agent can be done by adding to your Puppeteer code “setUser-agent” as follows:
const page = await browser.newPage();
await page.setUserAgent(‘Mozilla/5.0 (Windows NT 10.0; Win64; x64)
AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58.0.3029.110
Safari/537.36′);
For replacing your user-agent data, check out this website: networkinghowtos.com/howto/common-user-agent-list
Testing Your System for Fingerprints
After all the manipulations, you should check all your current fingertips that your browser leaves. We recommend using the following list of websites for this procedure.
When using Multiloginapp, please check each of your profiles individually.
Conclusion
The modern Internet is collecting tons of info on each individual user. To avoid successful fingerprinting of your system we recommend setting and verifying unique system configuration or using special tools described above. Once you do that you will have much better chances for safe anonymous browsing with your new proxies.
Our company specializes in providing dedicated datacenter proxies and residential IPs that are catered to your needs. We currently maintain a no-frills policy that lets us offer you proxies at the most affordable rates in the market. Please check out our website (privateproxy.me) to find a proxy-based solution that is right for you.
Top 5 posts


Say you are set out to buy a pair of rare Yeezy Supremes during the upcoming drop at Yeezy Supply. What do you reckon your chances are to get one pair for yourself and another one to flip on the side later on when the kicks become an undeniable classic? To tell you the truth your chances are rather thin and it does not have much to do with luck.